Introduction to OWASP Methodologies for Mobile Application Pentesting
- Published on
Post Date
- Authors

- Name
- Juan Urbano Stordeur
- X
- @juanurss

TL;DR; In this post, we want to introduce you to the OWASP Mobile Methodologies that we use as a standard to carry out the analysis of vulnerabilities in mobile applications. We will be explaining what its purpose is, and why it should be taken into consideration when developing a mobile application or performing a pentest, so lets start!
What is OWASP?
OWASP is a nonprofit foundation that works to improve the security of software. Its acronym stands for Open Web Application Security Project and it is a project created in 2001 that seeks to enforce the knowledge of security threats against web applications. In 2011, the community first launched the OWASP Top 10 Mobile, including the mobile platform, into this extended world of security research and threats, and, in 2018, the OWASP MASTG (Mobile Application Security Testing Guide) and the OWASP MASVS (Mobile Application Security Verification Standard).
Why OWASP?
In Just Mobile Security we believe that, in order to make your mobile application secure, there are certain principles that must be complied with, but why OWASP? We consider OWASP as one of the most complete pillars for mobile security, for it complies with the main standards that our assessment team apply in every pentest. For that reason, we are proud to state that our services always comply with the OWASP top 10 Mobile MASTG (Mobile Application Security Testing Guide) and MASVS (Mobile Application Security Verification Standard).
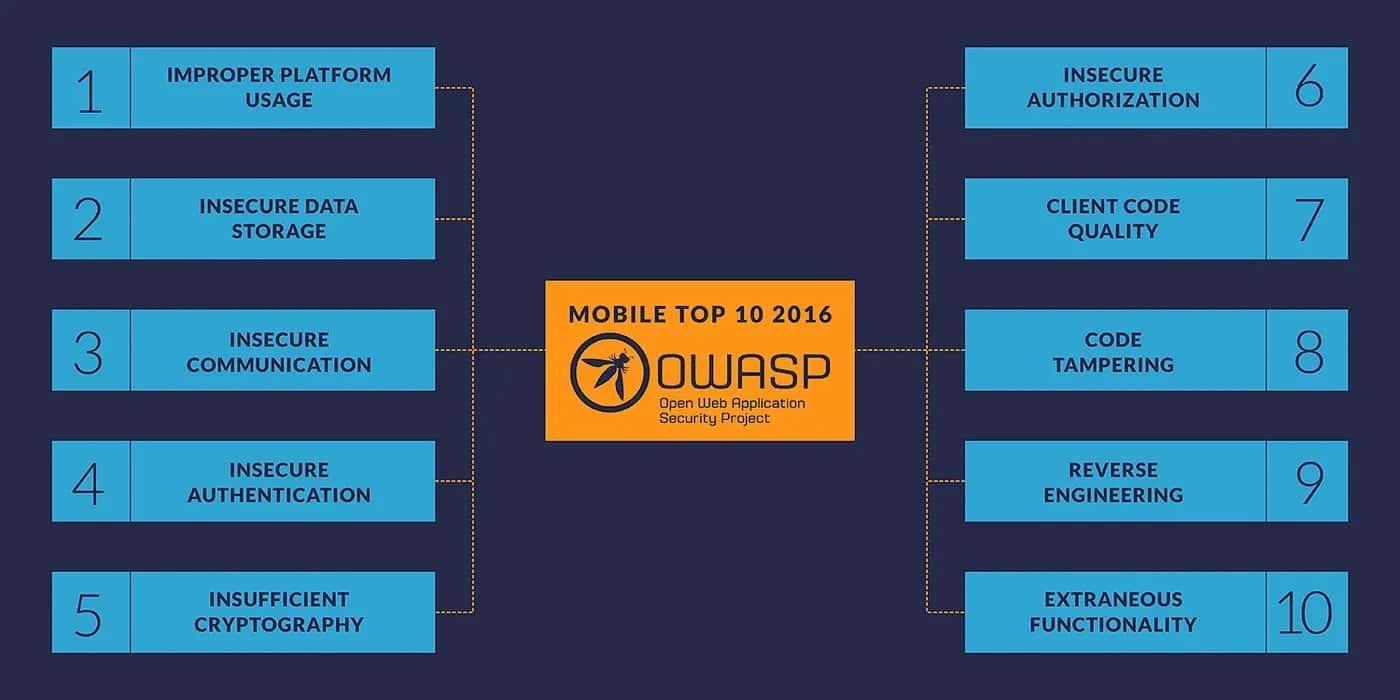
What is OWASP Top 10 Mobile?
Let’s focus on the Top 10: what is it? The OWASP top 10 mobile is essentially a guideline that you can refer to whenever you are both developing an application and performing a pentest. It comes with the Top 10 concurrencies of security flaws that are found in applications now days, so we will be soon explaining how you can make use of each topic to detect in advance possible security risks and mitigate them.
What is the OWASP MASTG?
The OWASP Mobile Application Security Testing Guide, as its name suggests, is a comprehensive manual for mobile app security testing and reverse engineering. It describes technical processes for verifying the controls listed in the OWASP Mobile Application Verification Standard (MASVS). The MASTG comes with several contents that are explained and solved in both static and dynamic ways, lots of examples, challenges, and exercises for you to practice to gain the knowledge you need to become a Professional Mobile Pentester.
Basically, for us, it is the Bible for Mobile Pentesting on which we base every assessment we perform, seeking to test every topic that it contains.

The MASTG comes with the following topics, processes, techniques, and tools:
General Testing Guide
Including Mobile Application Taxonomy, Mobile Application Security Testing, Mobile App Tampering and Reverse Engineering and more topics for general Mobile Application Testing.
Android and iOS Testing Guide
Including Platform Overview, Basic Security Testing, Tampering and Reverse Engineering and more topics for both Android and iOS Application Testing.
Tools
Including all the tools that you might need to perform a Mobile Application Testing (from Frida, R2, jadx, apktool and more).
Crackmes
A complete package of both Android and iOS challenges for practicing and resolving.
References
With all the supplementary reading that you can use to reinforce your knowledge about Mobile Security.
What is the OWASP MASVS?
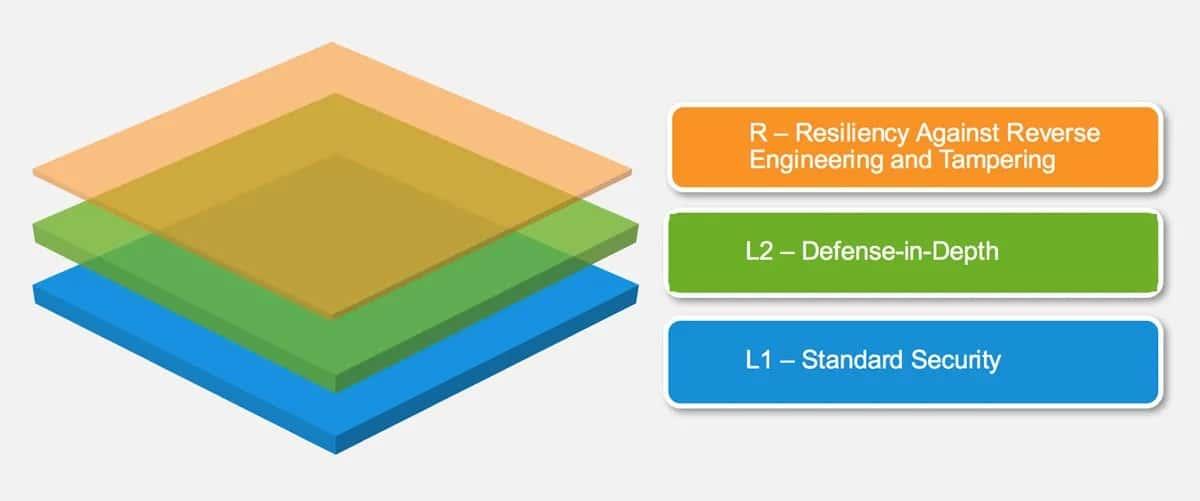
The OWASP Mobile Application Security Verification Standard is the industry standard for mobile app security. It can be used by mobile software architects and developers seeking to develop secure mobile applications, as well as security testers to ensure completeness and consistency of test results. The MASVS comes with solid information which is useful for analyzing applications step by step; such information is segmented in different levels to guarantee comprehension and help understand in which way an application can be analyzed. It is based on eight Security verification Controls, each one with its own Objective, Verification Requirements and References.
Try Tungstenic: Next-level mobile application vulnerability protection.
Contact Us
If you need to analyze your application contact us here:
sales@justmobilesec.com | Sales
Any other doubts or questions, don’t hesitate to write to us!
info@justmobilesec.com | Contact
Work with us!